F5 Firewall Solutions > Advanced Multi-Layer Firewall Protection > Module 1: F5 Multi-layer Firewall Source | Edit on
Getting Started¶
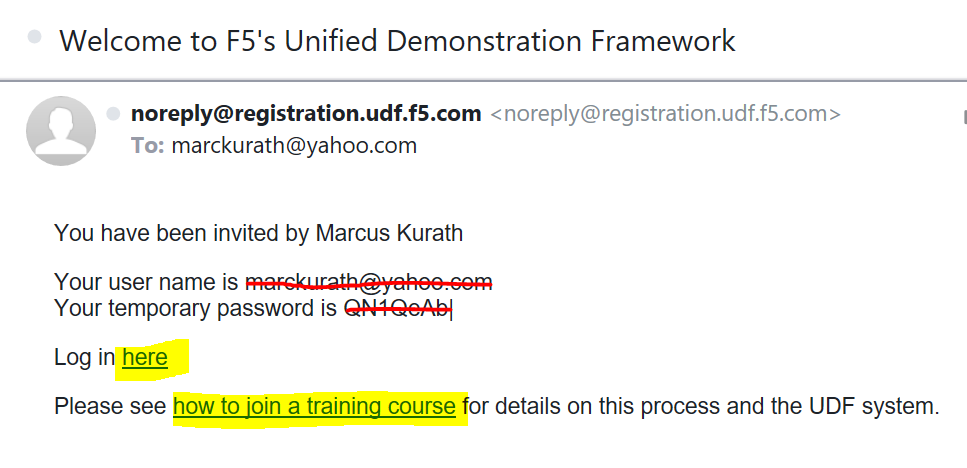
Check your email for an invitation from noreply@registration.udf.f5.com (Check your SPAM folder if you cant locate the email
The email will contain yur username and temporart Passwords
Click the how to join a training class
Note
You will not need to generate an SSH key for this course. All connectivity will be done from the “Jump Host”
Click the hyperlink Log in here
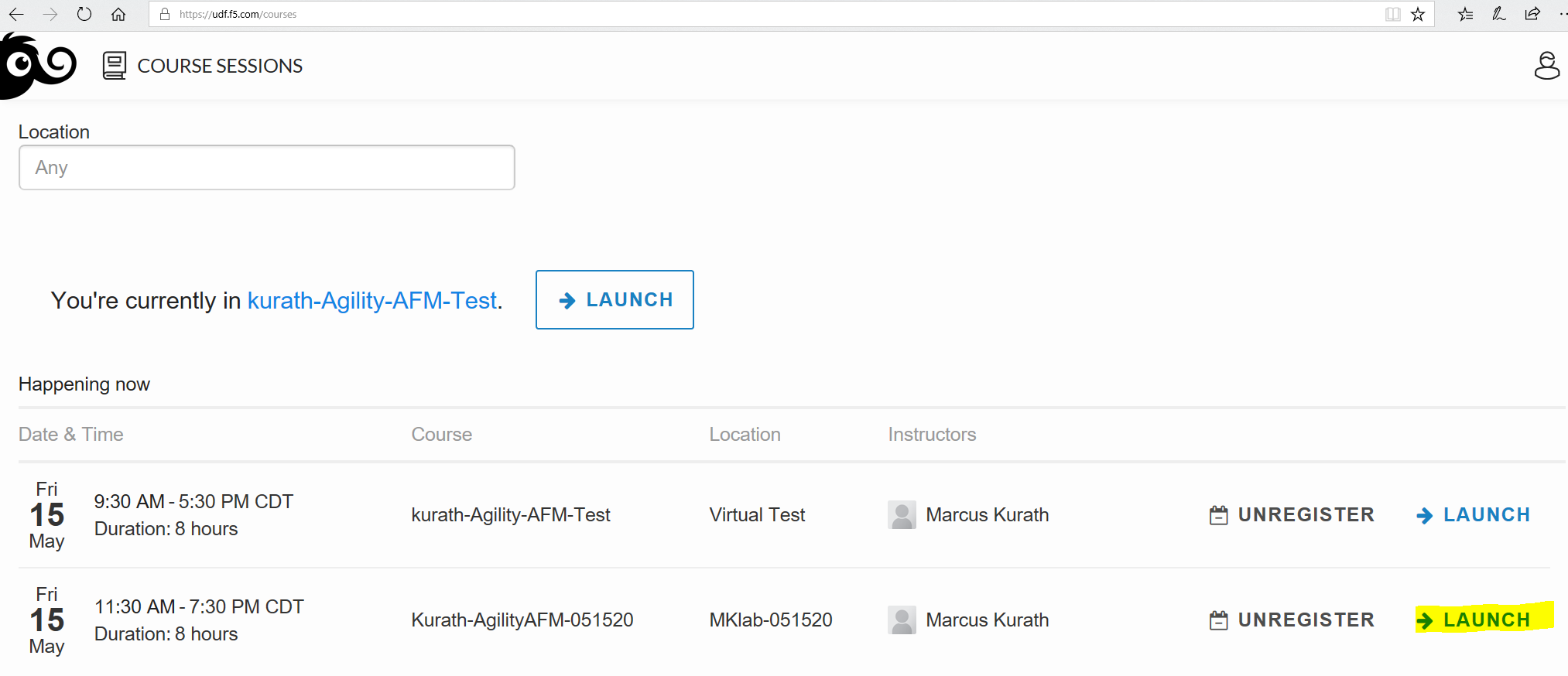
Select the course you wnat to take and press Launch
Press the blue Join button to enter the class
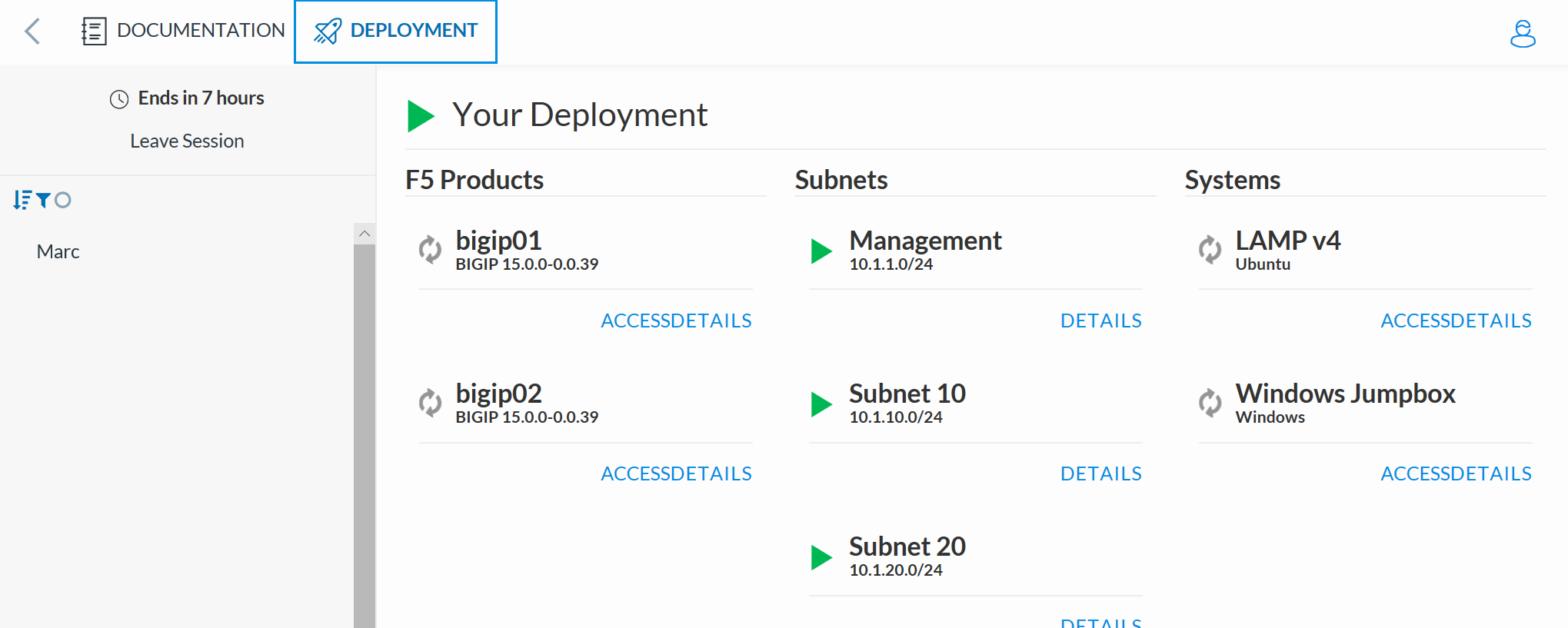
Review the Deployment Description
Select the Deployment Tab at the top of the screen
Wait about 10 minutes for the F5 Products and Systems to complete Startup
Note
The Windows Jump host takes a few minutes to complete startup.. Be patient even if it shows a green indication
Select the Access link below the Windows Jumpbox and select RDP and the correct resolution for your monitor
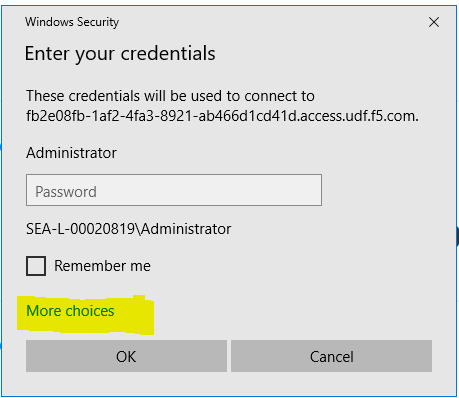
Select More Choices / Use A Different Account from the RDP login screen
Credentials
username: external_user
password: P@ssw0rd!
Note
Disregard the Licensing Error
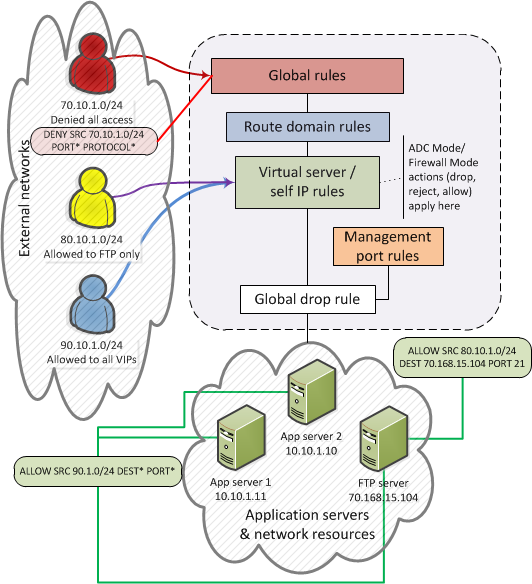
Firewall Rule Hierarchy¶
With the BIG-IP® Network Firewall, you use a context to configure the level of specificity of a firewall rule or policy. For example, you might make a global context rule to block ICMP ping messages, and you might make a virtual server context rule to allow only a specific network to access an application.
Context is processed in this order:
- Global
- Route domain
- Virtual server / self IP
- Management port*
- Global drop*
The firewall processes policies and rules in order, progressing from the global context, to the route domain context, and then to either the virtual server or self IP context. Management port rules are processed separately, and are not processed after previous rules. Rules can be viewed in one list, and viewed and reorganized separately within each context. You can enforce a firewall policy on any context except the management port. You can also stage a firewall policy in any context except management.
Tip
You cannot configure or change the Global Drop context. The Global Drop context is the final context for traffic. Note that even though it is a global context, it is not processed first, like the main global context, but last. If a packet matches no rule in any previous context, the Global Drop rule drops the traffic.
Tip
Use the Chrome Browser on the Jump Host desktop to configure BIG-IP 1 10.1.1.4. The login credentials are on the BIG-IP login page
Lab 1: Pre-configured pools and virtual servers¶
A virtual server is used by BIG-IP to identify specific types of traffic. Other objects such as profiles, policies, pools and iRules are applied to the virtual server to add features and functionality. In the context of security, since BIG-IP is a default-deny device, a virtual server is necessary to accept specific types of traffic.
The pool is a logical group of hosts that is applied to and will receive traffic from a virtual server.
On your personal device
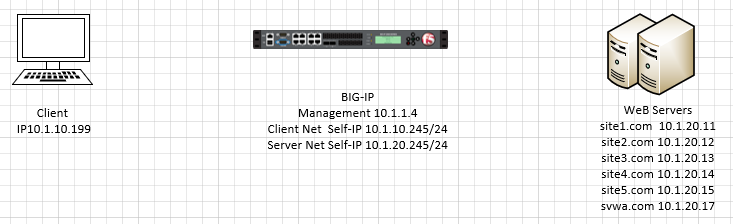
Look at the supplemental login instructions for:
- External Hostnames
- External IP addressing diagram
- Login IDs and Passwords are subject to change as well.
Note
Use the Chrome Browser to Connect to BIG-IP01— https://10.1.1.4 Credentials are displayed in the login screen
Inspect Application Pools¶
On BIG-IP
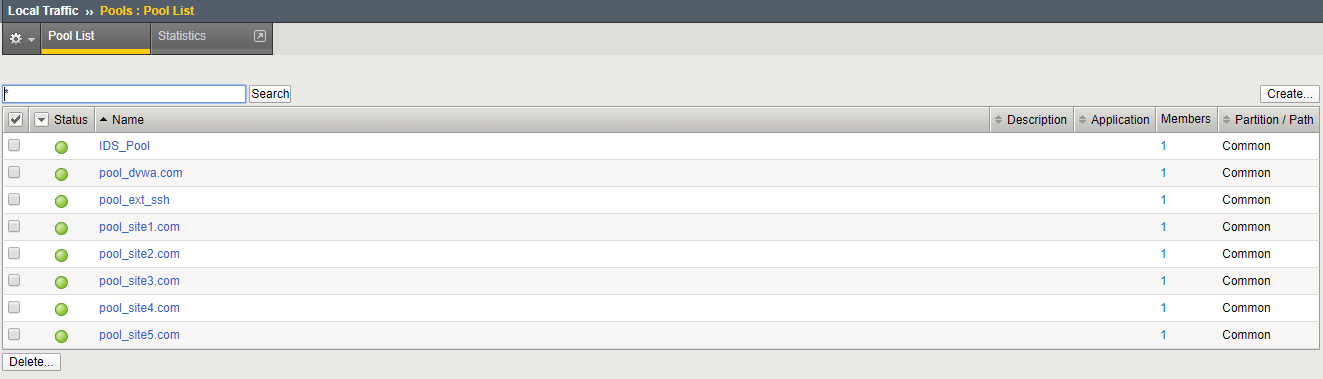
Verify the following pools using the following tabel of pool information.
Navigation: Local Traffic > Pools > Pool List
| Name | Health Monitor | Members | Service Port |
|---|---|---|---|
| pool_www.site1.com | http | 10.1.20.11 | 80 |
| pool_www.site2.com | http | 10.1.20.12 | 80 |
| pool_www.site3.com | http | 10.1.20.13 | 80 |
| pool_www.site4.com | http | 10.1.20.14 | 80 |
| pool_www.site5.com | http | 10.1.20.15 | 80 |
| pool_www.dvwa.com | tcp_half_open | 10.1.20.17 | 80 |
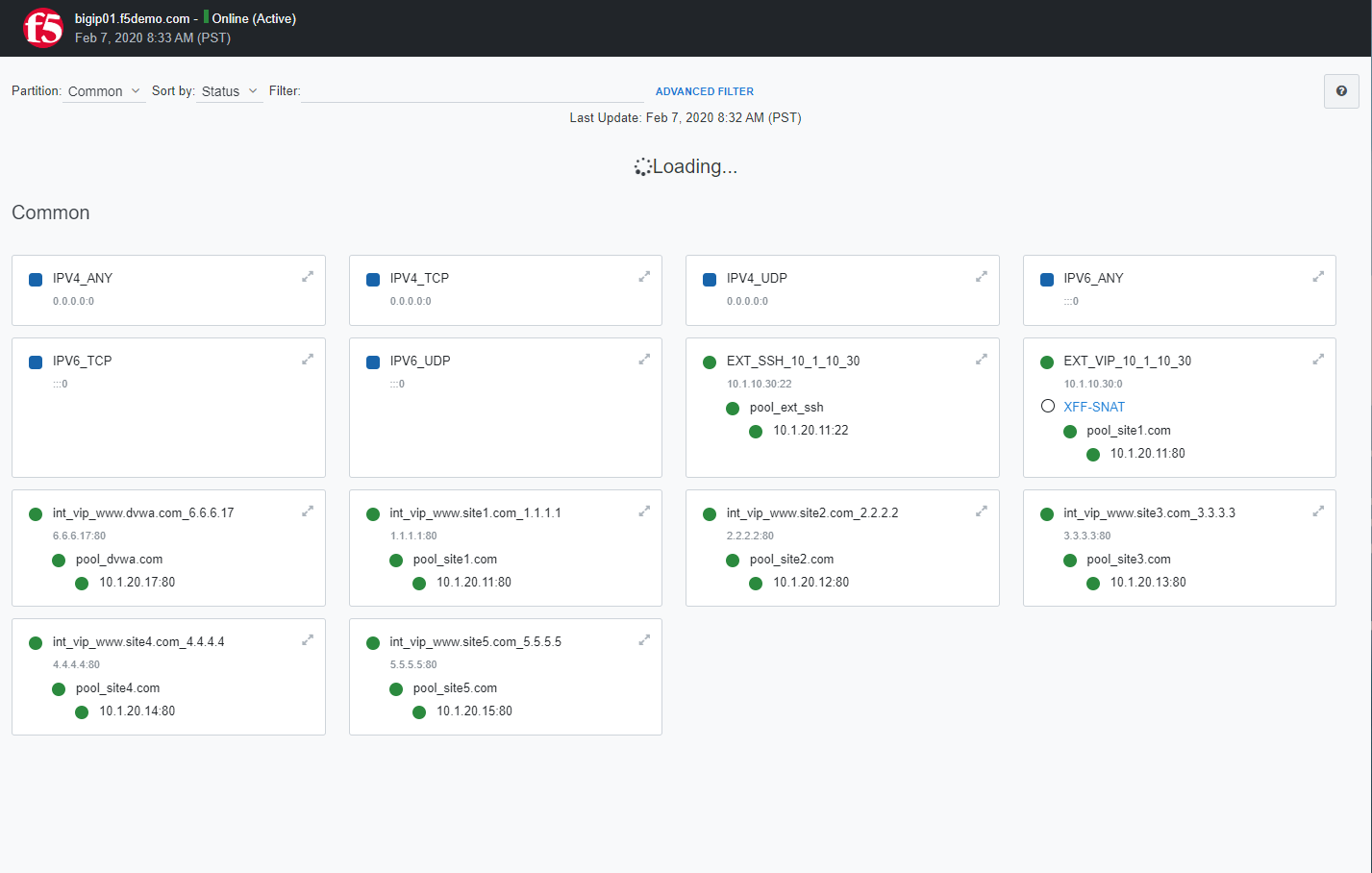
Inspect Application Virtual Servers¶
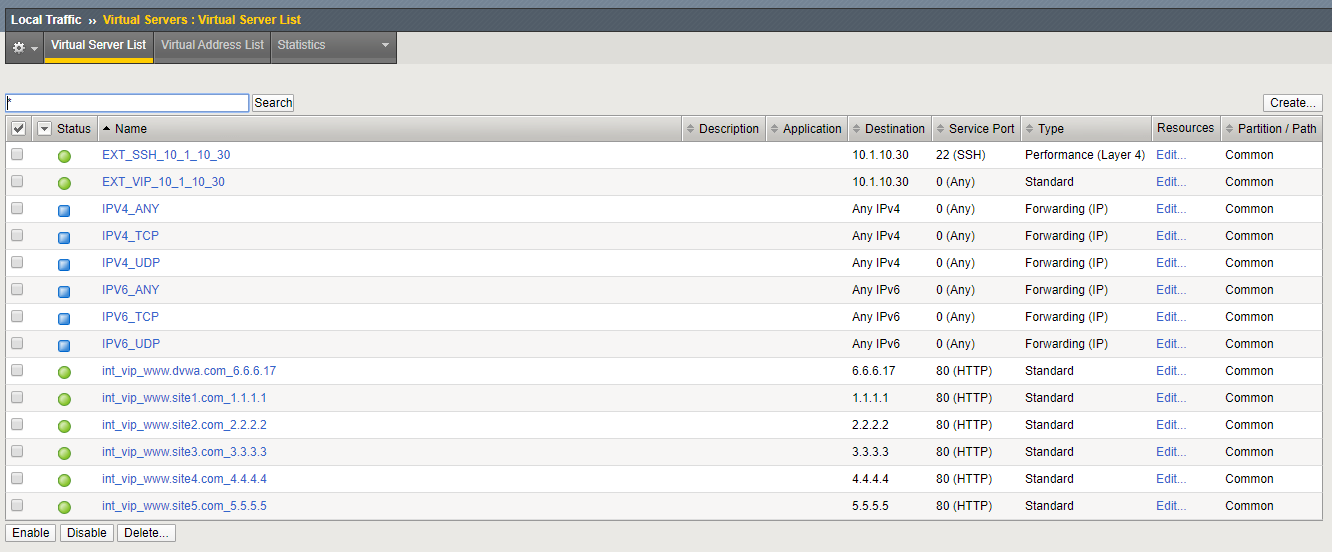
By using the term ‘internal’ we are creating the virtual servers on what is essentially a loopback VLAN which prevents them from being exposed. The EXT_VIP in this exercise is used to forward traffic with specific characteristics to the internal VIP’s. This is accomplished by assigning a traffic policy to the VIP. The traffic policy is described and inspected in the next section. For this class, the Wildcard Virtual servers (Blue Square status indicator) are not used.
Navigation: Local Traffic > Virtual Servers > Virtual Server List
Inspect the Local Traffic Network Map
Navigation: Local Traffic > Network Map
Note
The virtual servers should show a green circle for status.
Note
This completes Module 1 - Lab 1