F5 Firewall Solutions > [Archive1] AFM - The Data Center Firewall > Lab 1 – Advanced Firewall Manager (AFM) > Creating AFM Network Firewall Rules Source | Edit on
Test the New Firewall Rules¶
Once again you will generate traffic through the BIG-IP AFM and then view the AFM (firewall) logs.
- Ping 10.1.20.11, 10.1.20.12, 10;120.13, 10.120.14, and 10.1.20.15 (why does ths work?)
- Open a new Web browser and access http://10.1.20.11
- Open a new Web browser and access https://10.1.20.11 (this should fail–why?)
- Open a new Web browser and access https://10.1.20.14
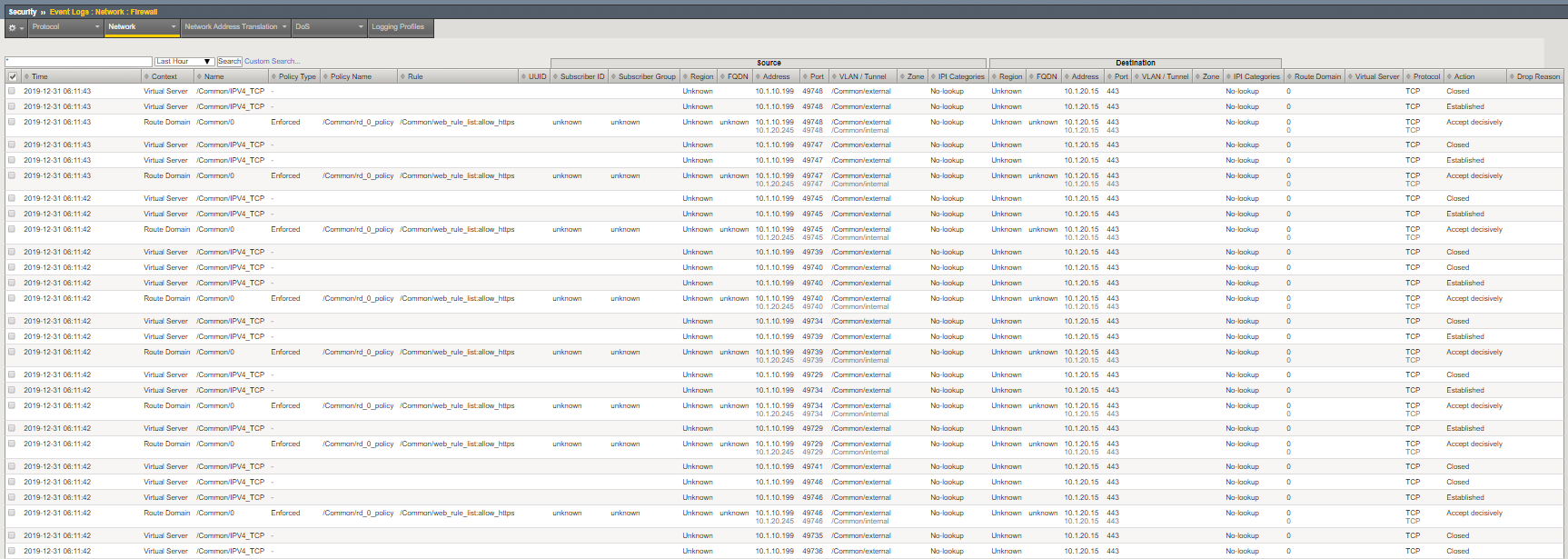
In the Configuration Utility, open the Security > Event Logs > Network > Firewall page.
Access for ports 80 / 443 was granted to a host using the web_rule_list: allow_http and allow_https rule.
Note the source address of the user (10.1.10.199). The IP forwarding VIPs are configured with SNAT auto-map. Packets forwarded by the BIG-IP to the servers have a source address 10.1.20.245. This arrangement is common in cloud deplouments since it simplifies traffic routing.
Denied connections are not logged in this configuration. These are dropped by the final reject rule in the global policy
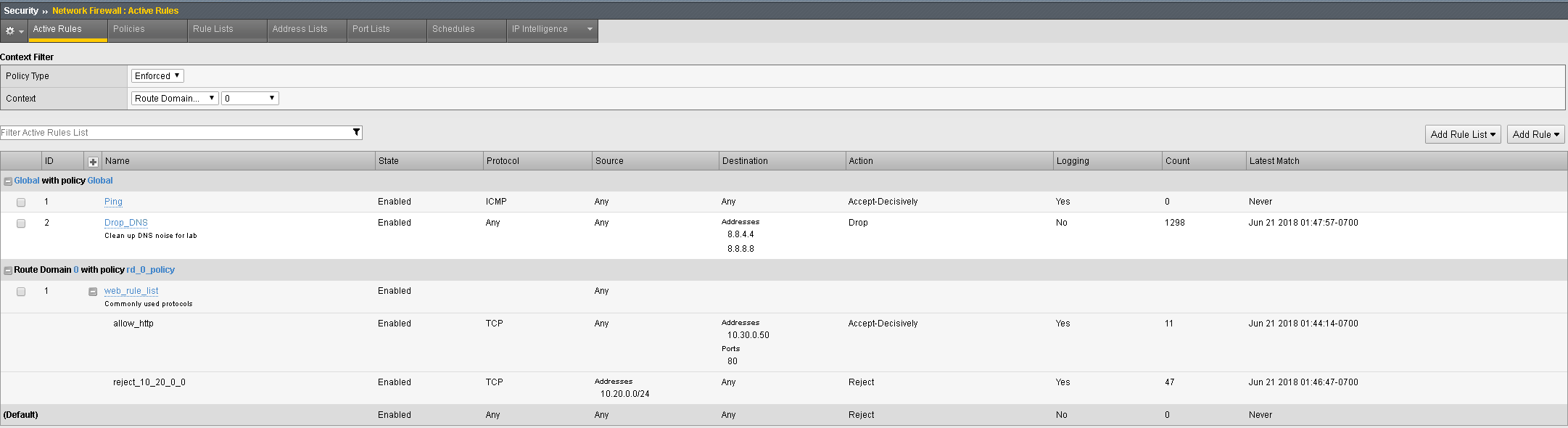
You may verify this, by going to Security > Network Firewall > Active Rules, then selecting the context for route domain 0. Note the Count field next to each rule as seen below. Also note how each rule will also provide a Latest Matched field so you will know the last time each rule was matched: (Investigating Counter behavior)