F5 Firewall Solutions > [Archive1] AFM - The Data Center Firewall > Lab 1 – Advanced Firewall Manager (AFM) > Creating AFM Network Firewall Rules Source | Edit on
Create a Rule List¶
Rule lists are a way to group a set of individual rules together and apply them to the active rule base as a group. A typical use of a rule list would be for a set of applications that have common requirements for access protocols and ports. As an example, most web applications would require TCP port 80 for HTTP and TCP port 443 for SSL/TLS. You could create a Rule list with these protocols, and apply them to each of your virtual servers.
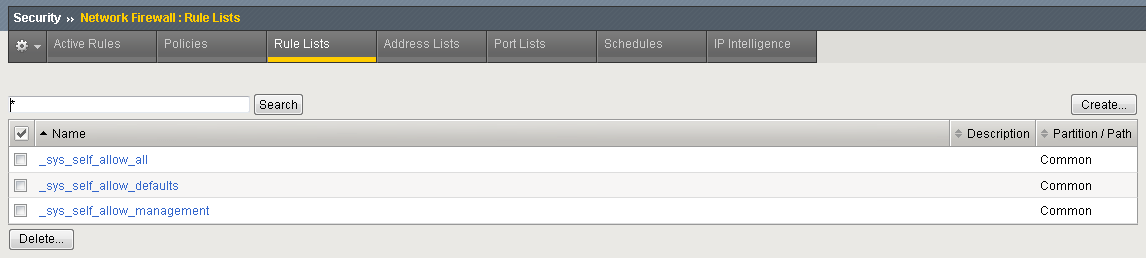
Let’s examine some of the default rule lists that are included with AFM.
Go to Security >Network Firewall > Rule Lists. They are:
- _sys_self_allow_all
- _sys_self_allow_defaults
- _sys_self_allow_management
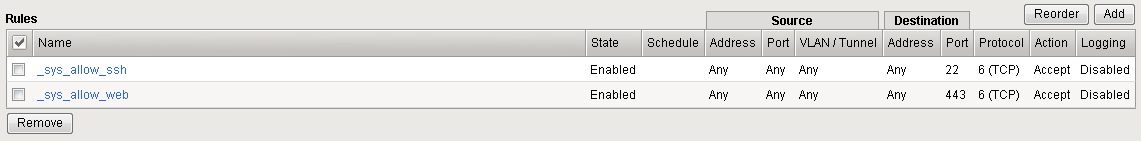
If you click on _sys_self_allow_management you’ll see that it is made up of two different rules that will allow management traffic (port 22/SSH and port 443 HTTPS). Instead of applying multiple rules over and over across multiple servers, you can put them in a rule list and then apply the rule list as an ACL.
On bigip01.f5demo.com (10.1.1.4) create a rule list to allow Web traffic. A logical container must be created before the individual rules can be added. You will create a list with two rules, to allow port 80 (HTTP) to servers 10.1.20.11 through 10.1.20.13 and another to allow port 443 (HTTPS) to servers 10.1.20.13 through 10.1.20.15. First you need to create a container for the rules by going to:
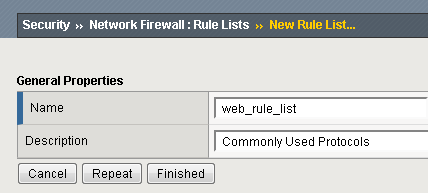
Security > Network Firewall > Rule Lists and select Create.
For the Name enter web_rule_list, provide an optional description and then click Finished.
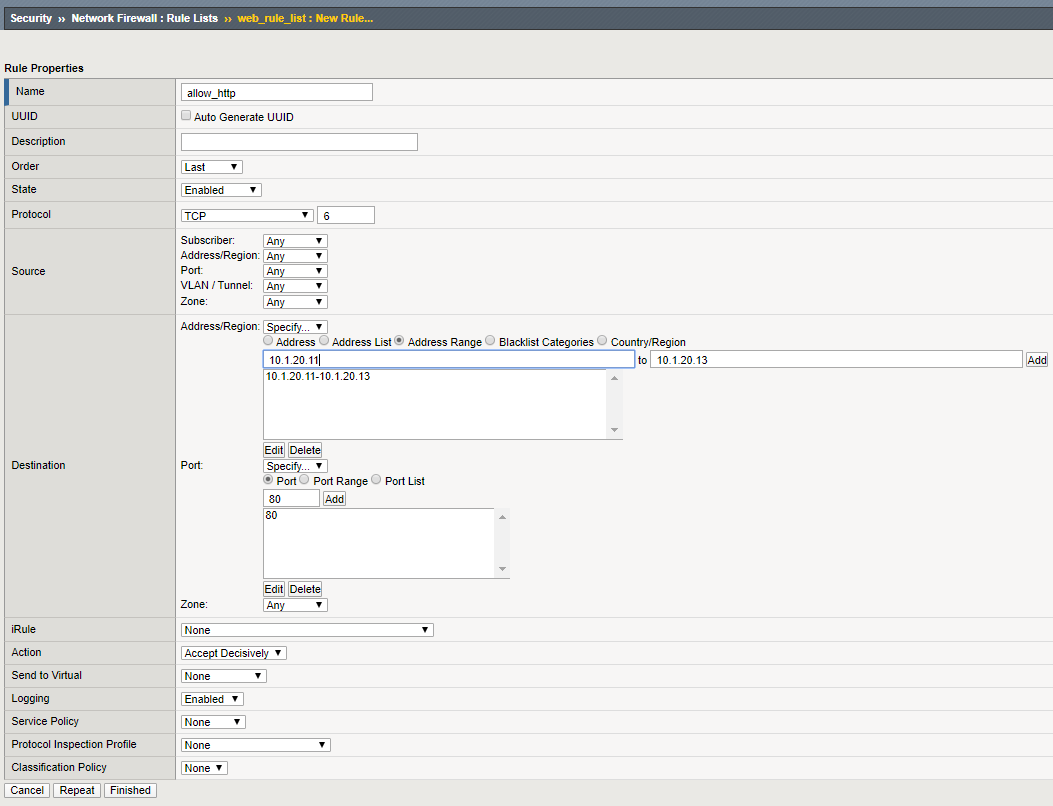
Edit the web_rule_list by selecting it in the Rule Lists table, then click the Add button in the Rules section. Here you will add two rules into the list; the first is a rule to allow HTTP.
| Name | allow_http |
|---|---|
| Protocol | TCP |
| Source | Leave at Default of Any |
| Destination Address | Specify…10.1.20.11, 10.1.20.13 then click Add |
| Destination Port | Specify… Port 80, then click Add |
| Action | Accept-Decisively |
| Logging | Enabled |
Select Repeat when done.
| Name | allow_https |
|---|---|
| Protocol | TCP |
| Source | Leave at Default of Any |
| Destination Address | Specify…10.1.20.14, 10.1.20.15 then click Add |
| Destination Port | Specify… Port 443, then click Add |
| Action | Accept-Decisively |
| Logging | Enabled |
Select Finished when completed.
When you exit, inspect the rule set. You’ll notice the reject rule is after the allow_https rule. This means that HTTP traffic to the servers on 10.1.20.0/24 will be accepted, while all other traffic to this subnet will be rejected based on the ordering of the rules. This is traditional default deny behavior