F5 Firewall Solutions > [Archive1] AFM - The Data Center Firewall > Lab 3 - AFM DDoS Lab > Advanced Firewall Manager (AFM) Detecting and Preventing System DoS and DDoS Attacks Source | Edit on
Simulating a Christmas Tree Packet Attack¶
Joanna was feeling festive this morning. In this example, we’ll set the BIG-IP to detect and mitigate Joanna’s attack where all flags on a TCP packet are set. This is commonly referred to as a Christmas Tree Packet and is intended to increase processing on in-path network devices and end hosts to the target.
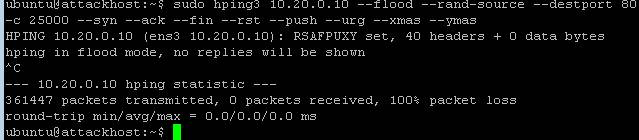
We’ll use the hping utility to send 25,000 packets to our server, with random source IPs to simulate a DDoS attack where multiple hosts are attacking our server. We’ll set the SYN, ACK, FIN, RST, URG, PUSH, Xmas and Ymas TCP flags.
In the BIG-IP web UI, navigate to Security > DoS Protection > Device Configuration > Network Security.
Expand the Bad-Header-TCP category in the vectors list.
Click on the Bad TCP Flags (All Flags Set) vector name.
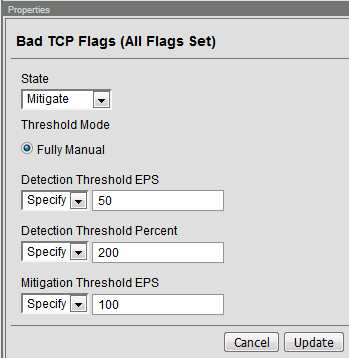
Configure the vector with the following parameters:
State: Mitigate
Threshold Mode: Fully Manual
Detection Threshold EPS: Specify 50
Detection Threshold Percent: Specify 200
Click Update to save your changes.
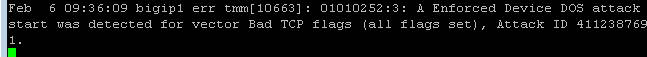
Open the BIG-IP SSH session and scroll the ltm log in real time with the following command: tail -f /var/log/ltm
- On the attack host, launch the attack by issuing the following command on the BASH prompt:
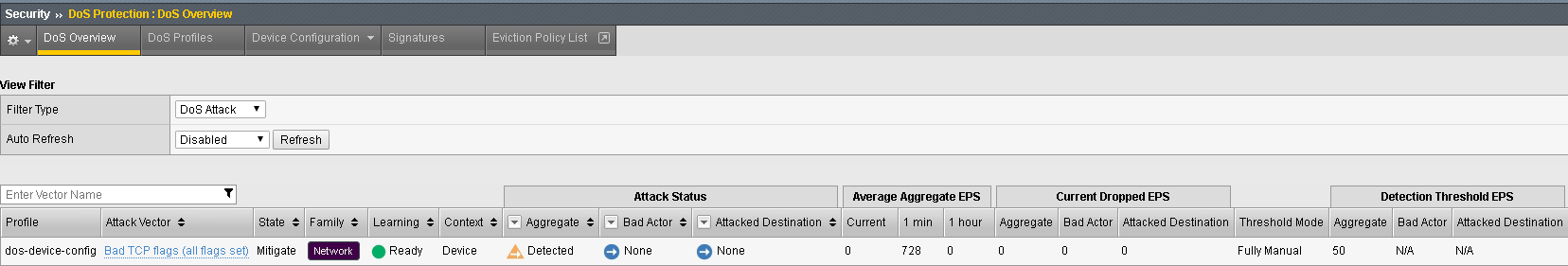
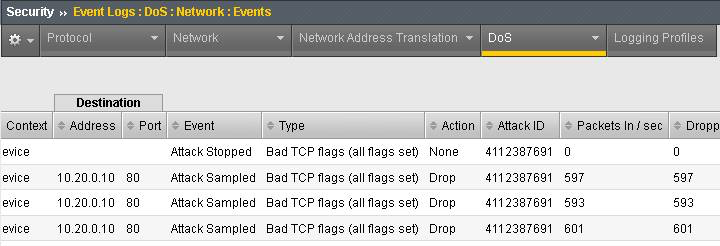
sudo hping3 10.20.0.10 --flood --rand-source --destport 80 -c 25000 --syn --ack --fin --rst --push --urg --xmas --ymas Navigate to Security > DoS Protection> DoS Overview (you may need to refresh or set the auto refresh to 10 seconds). You’ll notice from here you can see all the details of the active attacks. You can also modify an attack vector right from this screen by clicking on the attack vector and modifying the details in the fly out panel.
Navigate to Security > Reporting > DoS > Analysis. Single-click on the attack ID in the filter list to the right of the charts and observe the various statistics around the attack.