F5 Firewall Solutions > [Archive1] AFM - The Data Center Firewall > Lab 3 - AFM DDoS Lab > Detecting and Preventing DNS DoS Attacks on a Virtual Server Source | Edit on
Filtering specific DNS operations¶
The BIG-IP offers the ability to filter DNS query types and header opcodes to act as a DNS firewall. To demonstrate, we will block MX queries from our DNS server.
Open the SSH session to the Attack Host.
- Perform an MX record lookup by issuing the following command:
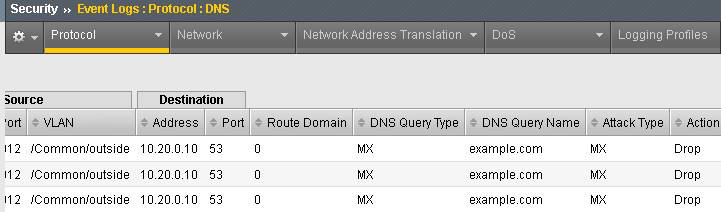
dig @10.20.0.10 MX example.com The server doesn’t have a record for this domain. This server doesn’t have MX records, so those requests should be filtered
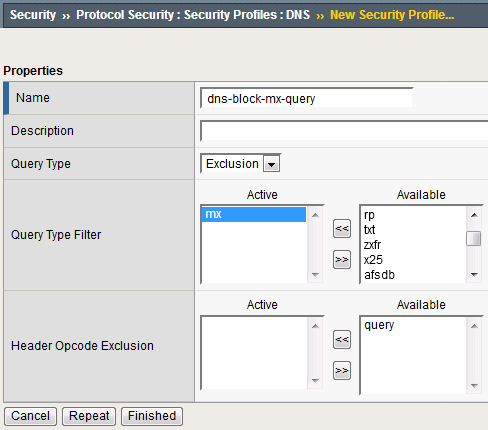
Navigate to Security > Protocol Security > Security Profiles > DNS and create a new DNS security profile with the following values, leaving unspecified attributes at their default value:
Name: dns-block-mx-query
Navigate to Local Traffic > Profiles > Services > DNS. NOTE: if you are mousing over the services, DNS may not show up on the list. Select Services and then use the pulldown menu on services to select DNS.
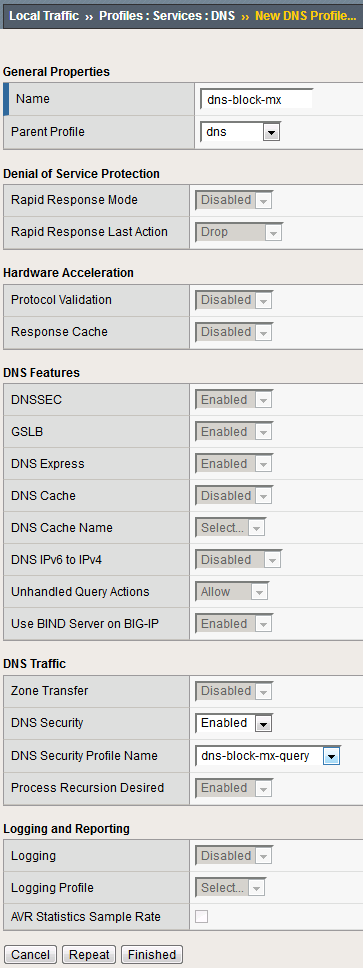
Create a new DNS services profile with the following values, leaving unspecified values at their default values:
Name: dns-block-mx
- DNS Traffic
DNS Security: Enabled
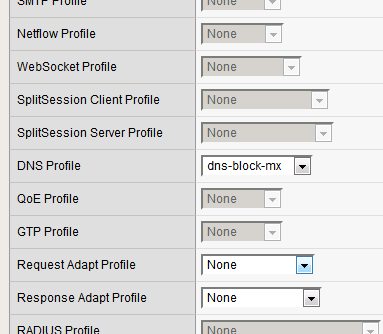
Navigate to Local Traffic > Virtual Servers > Virtual Server List.
Click on the udp_dns_VS virtual server name.
In the Configuration section, change the view to Advanced.
Click Update to save your settings.
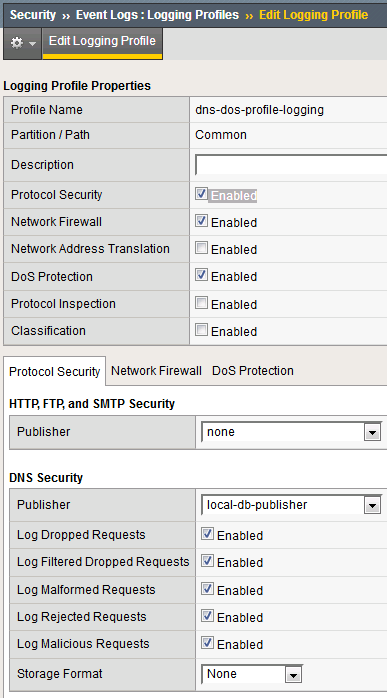
Navigate to Security > Event Logs > Logging Profiles.
Click on the dns-dos-profile-logging logging profile name.
Check Enabled next to Protocol Security.
Make sure that you click Update to save your settings.
- Return to the Attack Server SSH session and re-issue the MX query command:
dig @10.20.0.10 MX example.com The query hangs as the BIG-IP is blocking the MX lookup.
This concludes the DNS portion of the lab. On the Victim Server, stop the top utility by pressing CTRL + C. No mail for you Joanna!!