F5 Firewall Solutions > [Archive1] AFM - The Data Center Firewall > Lab 3 - AFM DDoS Lab > Detecting and Preventing DNS DoS Attacks on a Virtual Server Source | Edit on
Simulate a DNS DDoS Attack¶
Open the SSH session to the victim server and ensure the top utility is running.
- Once again, attack your DNS server from the attack host using the following syntax:
dnsperf -s 10.20.0.10 -d queryfile-example-current -c 20 -T 20 -l 30 -q 10000 -Q 10000 On the server SSH session running the top utility, notice the CPU utilization on your server remains in a range that ensures the DNS server is not overwhelmed.
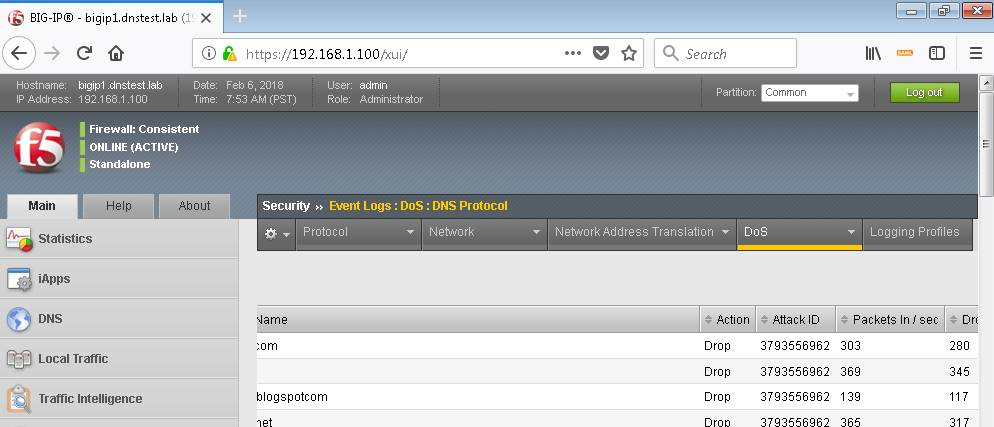
After the attack, navigate to Security > Event Logs > DoS > DNS Protocol. Observe the logs to see the mitigation actions taken by the BIG-IP. Be sure to scroll right…